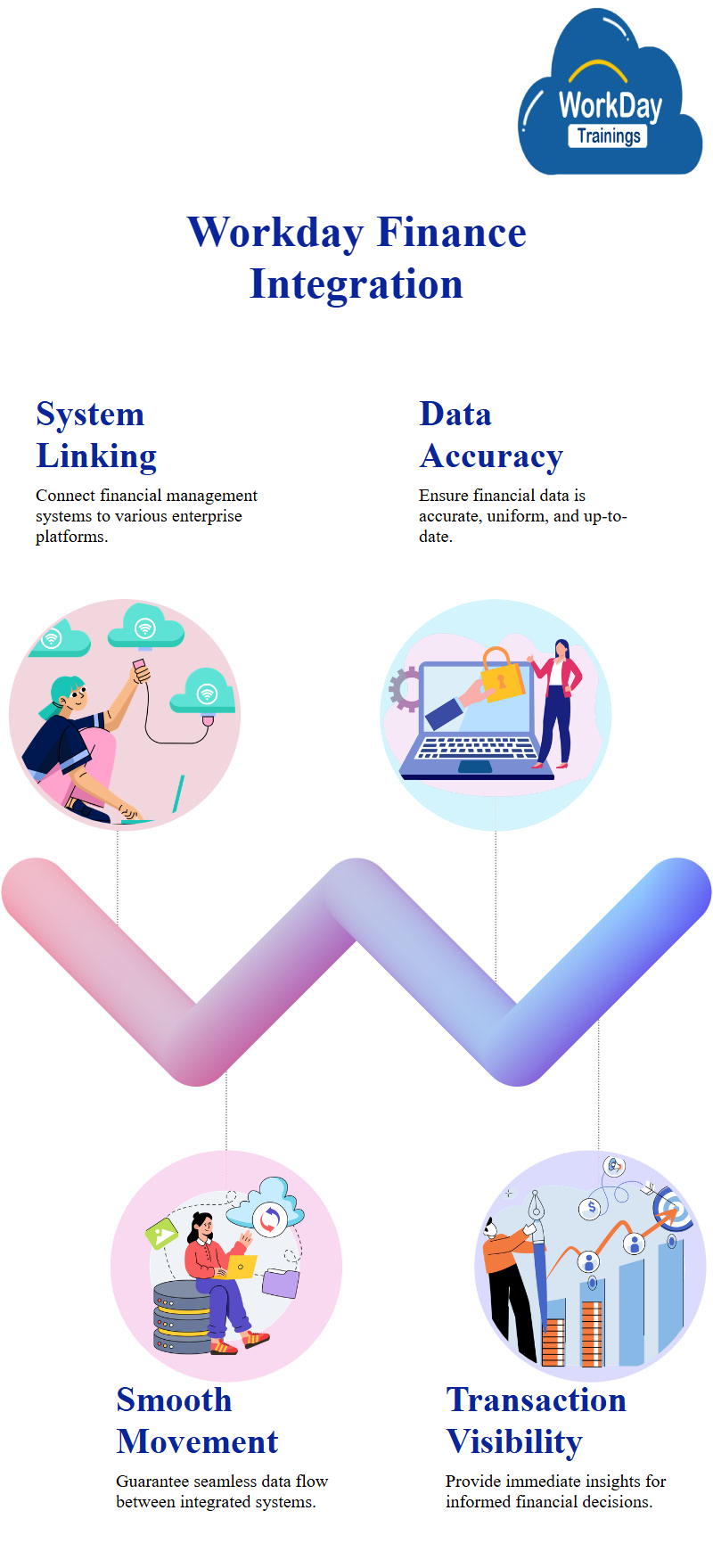
Workday Finance Integration allows enterprises to easily link their Workday financial management system with various systems, including their general ledger, accounts payable/receivable/inventory management platforms and inventory control system.
The integration ensures smooth data movement between systems while guaranteeing financial data’s accuracy, uniformity, and currency.
Additionally, it provides immediate visibility into financial transactions so firms can make informed decisions for their financial operations.
Role-Based and User-Based Approaches to Workplace Security Groups
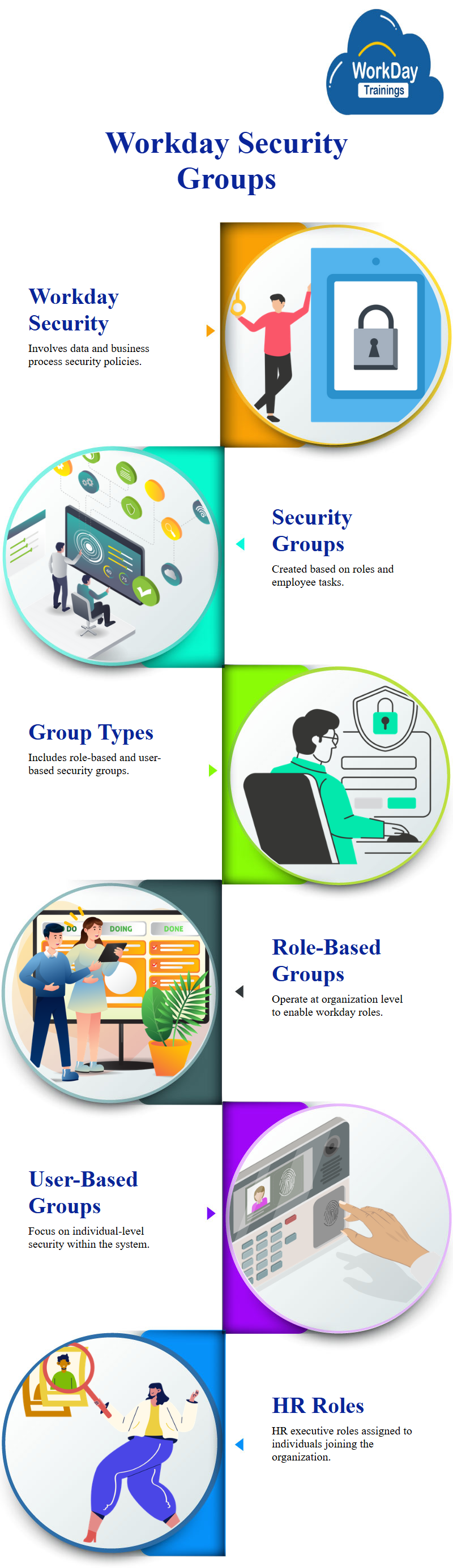
Workday Security is a complex process involving data security and business process security policy on workdays.
Workday Security is given to a security group created based on workday roles and employee tasks.
There are two main types of workday security groups: role-based and user-based.
Enabling Workday Role-Based Security Groups
Workday Role-based security groups work on the organization level, enabling workday roles.
For example, an HR executive role is assigned to an individual who joins the workday organization as an HR executive.
Understanding Workday Organizations
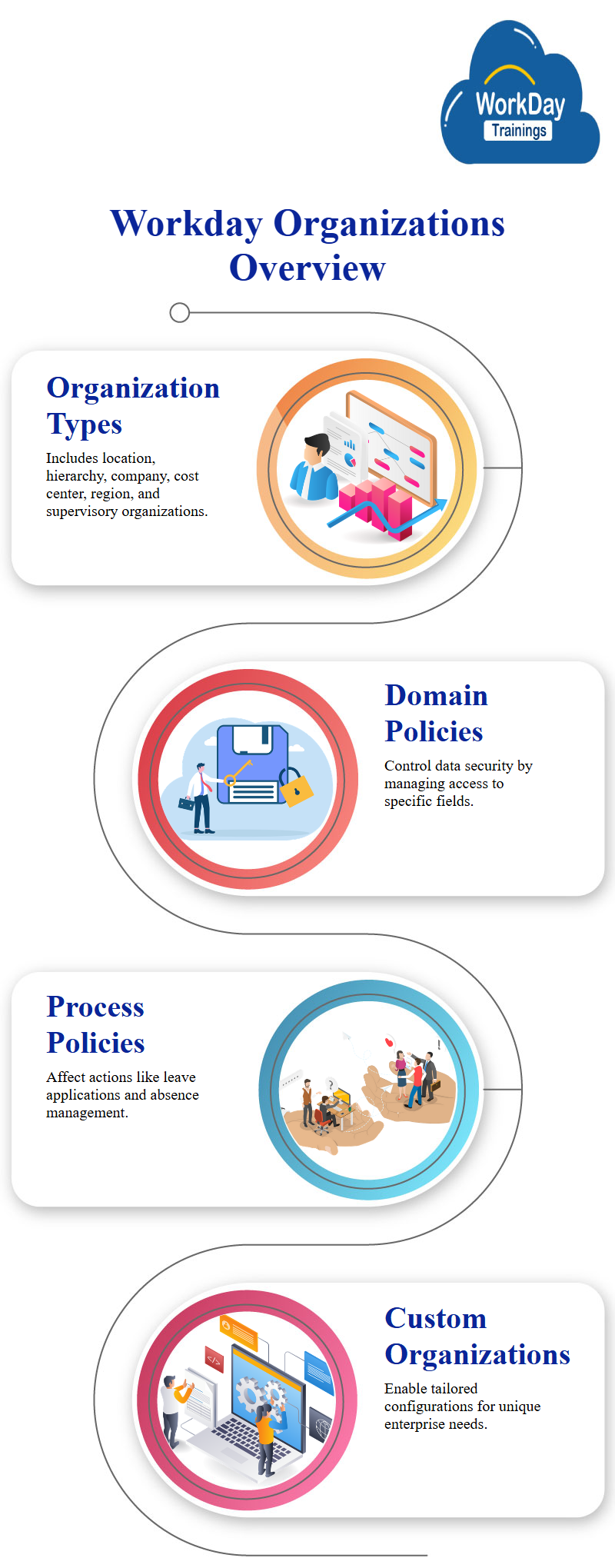
Each workday organization has eight types: location, location hierarchy, company workday company hierarchy, cost center hierarchy, area and region hierarchy, custom organization’s, and supervisory workday organizations.
Managing Data Security with Domain and Business Process Policies
Domain security policies help manage data security by controlling access to specific fields, such as viewing, modifying, or not seeing particular fields.
Business process policies influence actions like applying for leaves or leaving absences.
Workday Domain Security Policy: Managing Access to Data in Different Functional Areas
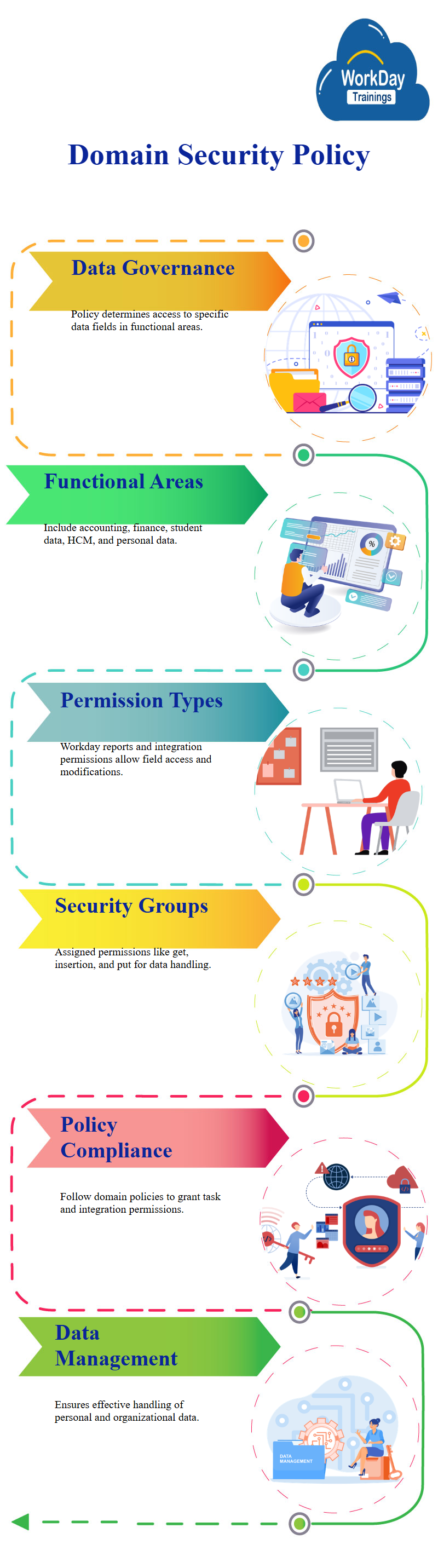
Data security is governed by domain security policy, a collection of fields allowing you to decide which data you should access.
Workday has different functional areas, such as the accounting center, finance, and personal data.
The report explains these functional areas, including Workday student, HCM module, accounting center, finance, and personal data.
Workday Types, Security Groups & Domain Security Policies in Personal Data Management
Permissions are given through domain security policies for workday reports and tasks, integration and integration permission.
To grant permissions, you need to follow the domain security policy of the functional area.
Coming to the point of permissions in personal data management. They discuss two types of permissions: workday reports and tasks permissions, which allow users to access specific fields, and integration permissions, which enable users to view and modify data.
This explains that security groups are given permissions, such as get, insertion, and put.
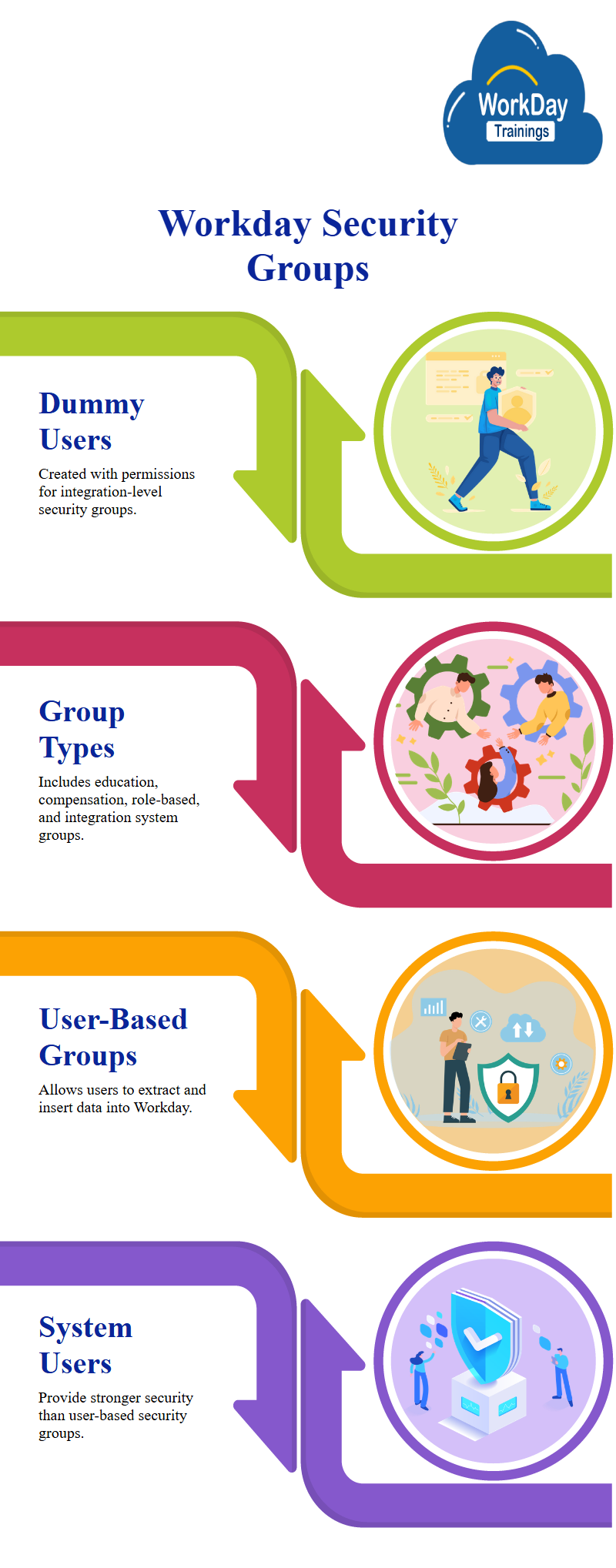
Understanding and Managing Security Groups in Workday
A dummy user with all necessary permissions for integration-level security groups is created.
This user can be assigned to a specific role-based security group with all the required permissions.
These emphasize the importance of understanding how security is given and the types of security groups created.
Multiple security groups exist, including workday education, compensation, conditional role-based, and integration system security groups.
When creating a security system user, the permissions are given to the specific user, and these roles become essential for them, too.
Creating a user-based security group is essential, allowing users to extract and insert data from the workday.
However, they caution that creating a user-based security group may not guarantee the same level of security as creating a system user.
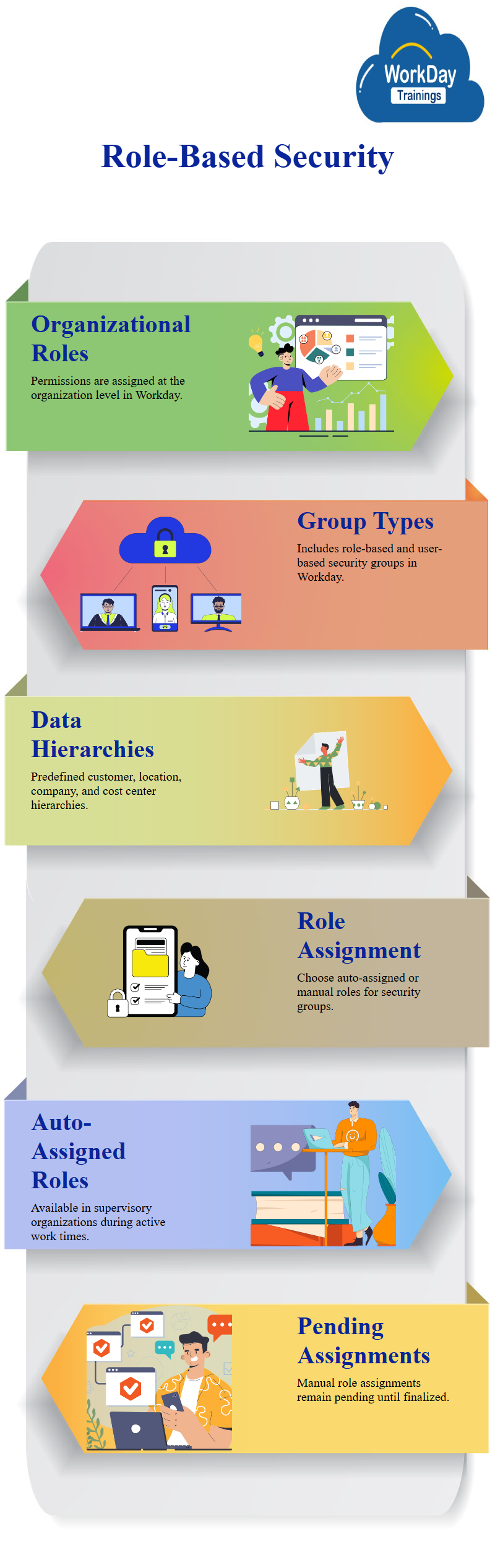
Understanding Role-Based Security Groups in Workday
Permissions are given to security groups in Workday, which are based on the organization level.
There are two significant types of security groups: role-based and user-based. Role-based security groups’ workdays work on the organization level, with three types of information: predefined customer, location company, cost center and region, and hierarchy.
It would be best if you first made it at the organization level to create a role-based security group.
You can choose whether to assign the role as an auto-assigned role or if you want to give it manually.
Auto-assigned roles are available in every supervisory organization during work time, while workday manual assignments are pending.

Prasanna
Knowledge is not the ultimate goal of education, action is.

