Workday Security Roles Inheritance in Organizations
A Workday security group is a group of users who need the same access, such as an HR partner or role-based Workday security group. Roles are always assigned to an organization, and in supervisory Workday organizations, roles can be assigned to unfilled positions. If a role is not filled, it is inherited from the superior organization.
For example, if a position is unfilled, the manager of the supervisory Workday organization is assigned to the manager of the Workday supervisory organization, which is the manager of IT sales in Asia Pacific.
The Workday manager’s name is Jack, and the role is currently occupied by a person named Prin. If the position is framed up, it will be inherited by Praveen, who will act as the Workday manager.
This concept of Workday roles and positions is crucial in managing Workday security and ensuring the Workday security of sensitive information.

Importance of Role Assignment in Organizations
This topic discusses the importance of assigning roles to specific positions or individuals within an organization. It is the use of single assignment roles, which allow for only one position to be assigned to a role.
This is useful for supervisory organizations, where multiple people can be assigned to a role.
However, the Workday advantage of having multiple people assigned as HR partners is that they can take action if a task is waiting on them.
Managing Users in a Security Group: Benefits and Best Practices
A security group is a group of users with the same access, which can be beneficial in certain situations. However, it is important to note that assigning roles to multiple individuals does not necessarily mean that all of them must take action.
Instead, assigning roles to specific individuals can help maintain consistency and efficiency within the organization.
Role-Based Access and Security: Workday HR Partner Roles and Constrained Security Groups
This explains that all individuals within an organization have the same level of access to the HR partner role, regardless of their management level or length of service.
This is known as a role-based security group, where permissions are granted by virtue of the role assigned. Workers can also have permissions by virtue of their assigned role. However, if a supervisory organization requires multiple managers, it is technically possible.
The single assignment rule manager is not possible, but a role can be assigned to multiple people or positions. The task used to create the role is maintained, and the task used to update the role is the same.
To change the role, the same task is used, and the changes are made to the settings, such as hiding on view, self-assignment, or single assignment.
The task of maintaining assignable roles is the only one that requires attention. After creating a role, permissions are given to the roles through domain and Workday business process security policies.
Security groups are included in these policies, and the process of creating a security group is straightforward. A role-based security group is created, and the name is “double the Workday compensation partner.”
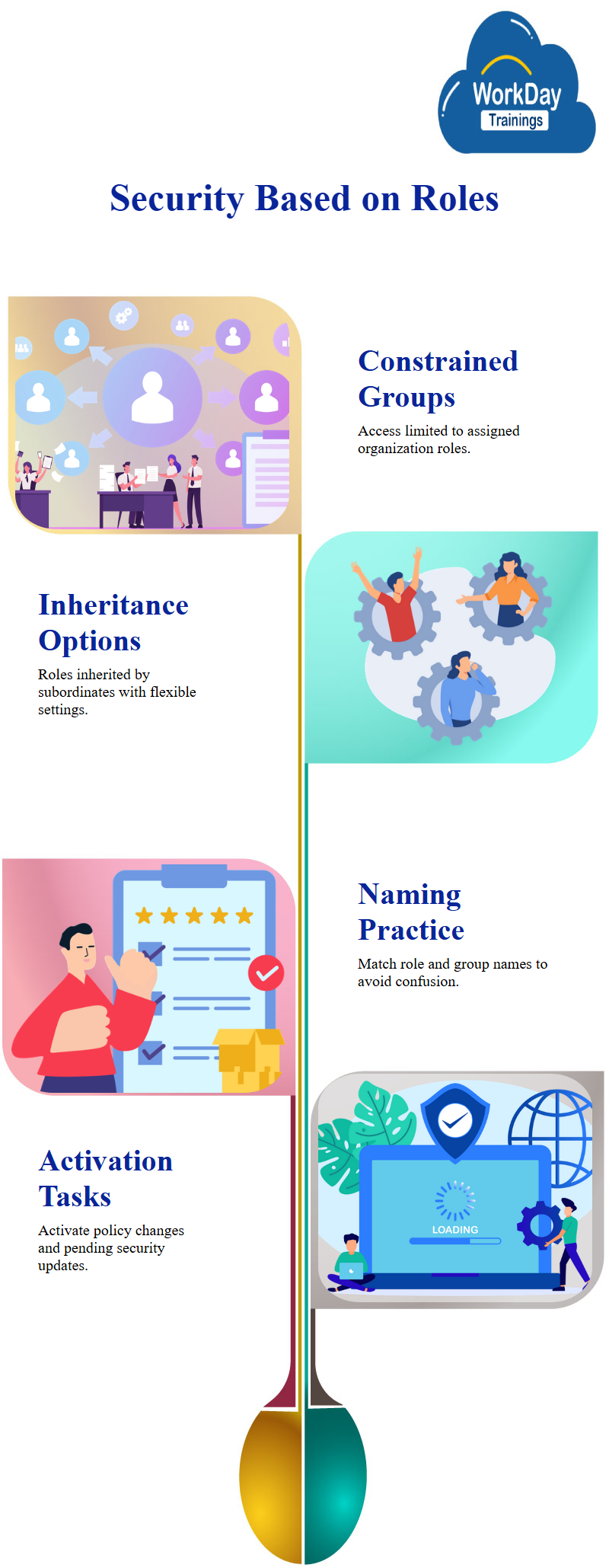
There are two types of security groups in the system: constrained and unconstrained. Constrained security groups have specific permissions to specific organizations, and access only works on the organizations where the manager has the role.
For example, a sales terminator manager has access to only the employees they manage, while a sales manager can terminate an employee in sales. To ensure access to only the organization where the manager has the role, a constrained security group is created.
When creating a constrained security group, only the assigned role has access to the organization. The role-based security group is typically associated with the role and has certain permissions in the security policies.
It is recommended to keep the name of the security group and the assignable role the same to make it easier to understand which role relates to which security group.
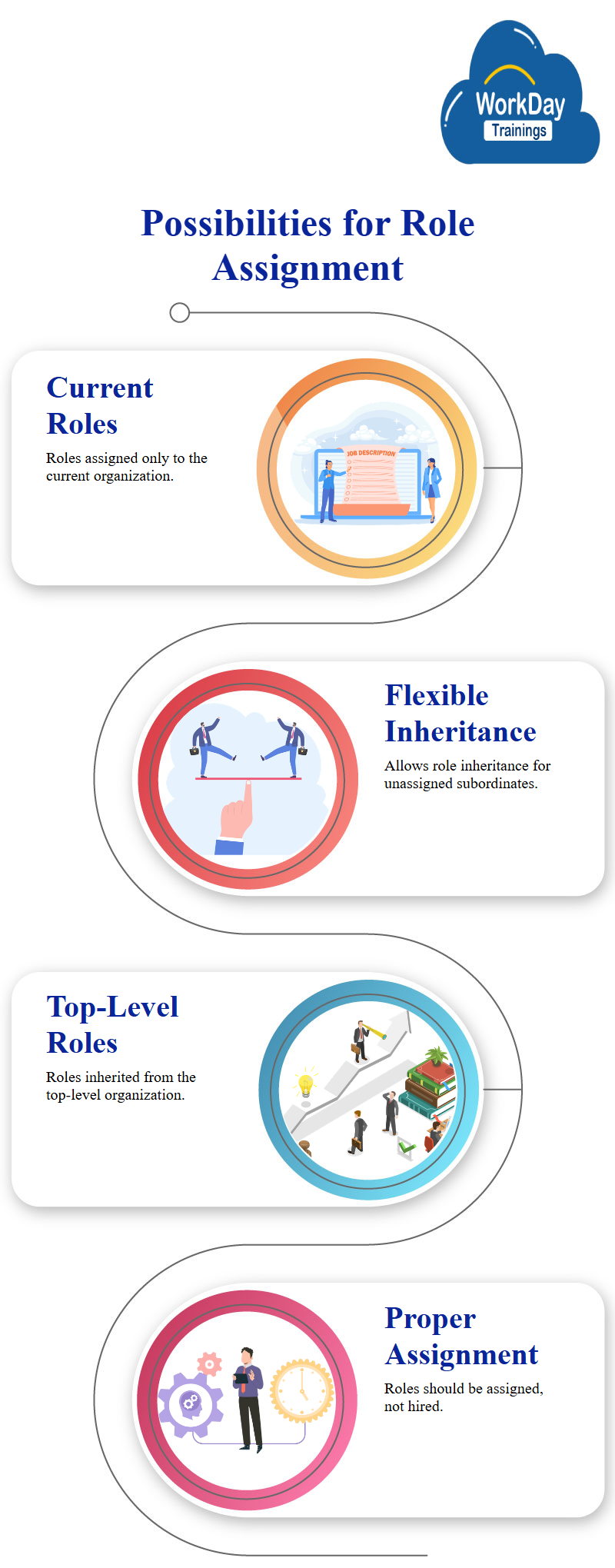
Role Assignment Options in Organizations: Which One to Choose?
The role assignment system in organizations highlights the default behavior of assigning roles to the current organization and any unassigned subordinates.
There are three options: no inheritance, default, and more powerful.
The first option applies to the current organization only, with all role assignments applied to the current organization.
The second option assigns the same role to all unassigned subordinates, regardless of previous role assignments.
The third option applies to the current organization and all subordinates, forcing the role to be inherited from the top-level organization.
The second option allows for a flexible level of subordinates to be inherited.
For example, if the organization has two subordinates, the manager of sales and manufacturing would be Daniel Paul. It also suggests that the role assignment system should be assigned to someone, not hired.
The Workday discusses the importance of assigning roles to the right person, rather than hiring someone.
Maintaining Security Group Permissions: Role Creation and Access Control
The task involves maintaining permissions for a security group. Users choose to copy permissions from an existing security group to the compensation partner. They find that the HR partner has all the necessary permissions, but the compensation partner doesn’t need access to certain information.
They decide to choose whether to keep or remove certain permissions.
The security group is added to the compensation partner’s security group, which includes domain security policy permissions. Users can choose to keep or remove certain permissions, such as access to series and birthdays reports, worker data, exit engine views, and expense reports.
The security group now has the necessary permissions to perform certain tasks. The compensation partner is now allowed access to this information, but they need to activate the group to make necessary changes to the security policy permissions.
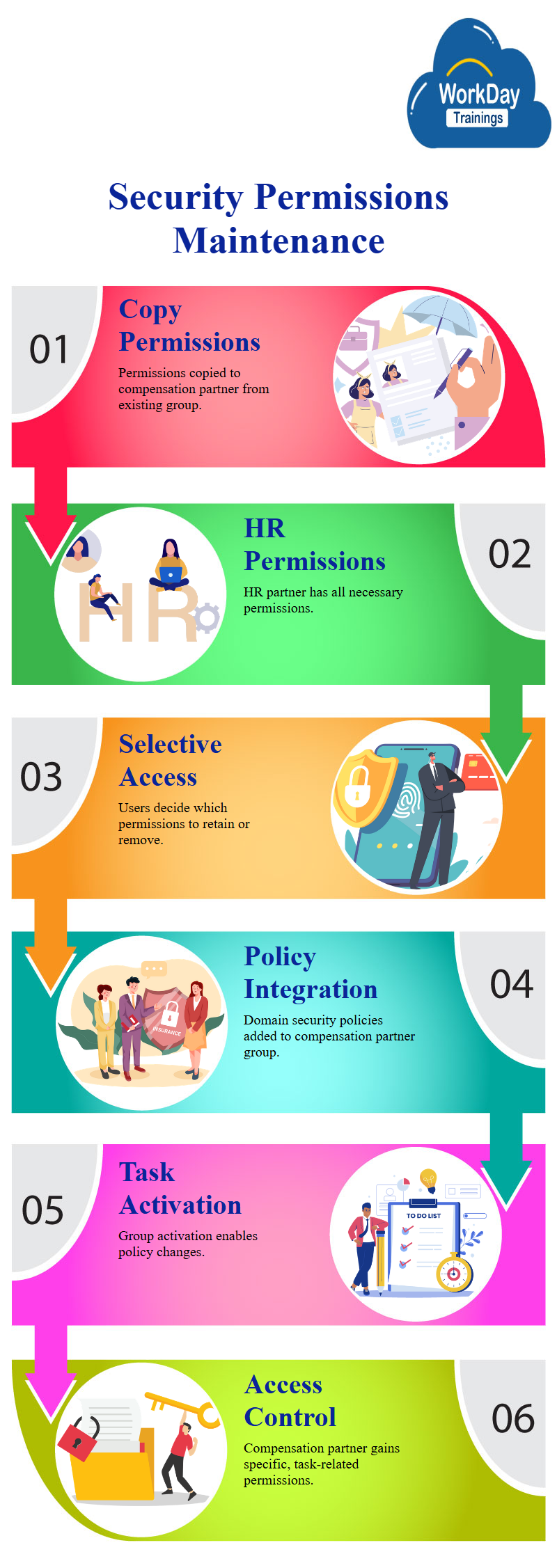
The task is pending. The security policy changes and the creation of a compensation partner role. The permissions from the HR partner to the compensation partner have been copied, and the role has been assigned to a security group.
The role has been assigned to multiple workers, including a Workday financial officer named Theresa. The compensation partner role is not restricted to a single assignment but can be assigned to multiple workers.
The role is inherited from the superior organization, and the Workday business process will be used to ensure equal access for all individuals involved.
With this, we can say that it is about the implications of the change and the potential implications for the organization.
Understanding Role-Based Security Groups: A Tutorial
The most common example of a role-based security group is a Workday manager, who is constrained by their role assignment and has access to only the organization where they have the role.
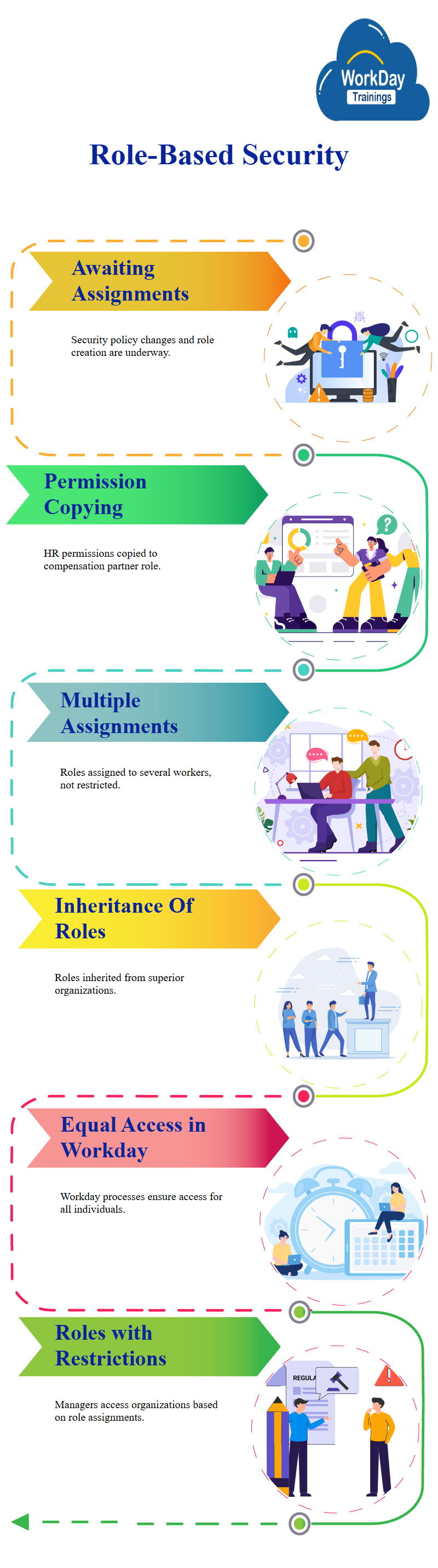
This type of Workday security group is constrained, meaning they only have access to the organization where they have the role. The typical behavior of role-based Workday security group and inheritance is that the role is inherited to the subordinate Workday organizations, with the default option being current organization and unassigned subordinates.
The other two options are forcefully inherited, which applies the role to the current Workday organization and all subordinates, and the last option is the number of levels. These options are crucial for understanding Workday security and ensuring that only the Workday organization where the role is assigned has access to the necessary information.
The concept of role-based security groups, is where a worker is assigned to a role within an organization. The role is linked to a security group, granting the worker access to certain things but constrained to the organization where they have the role.
Discussing the best practice in naming the role and security group, stating that the same name should be used to reduce confusion. The importance of activating a security group after making changes, that it requires two tasks: activate policy changes and activate pending security policy.
Understanding Role-Based Workday vs Workday. User-Based Security Groups
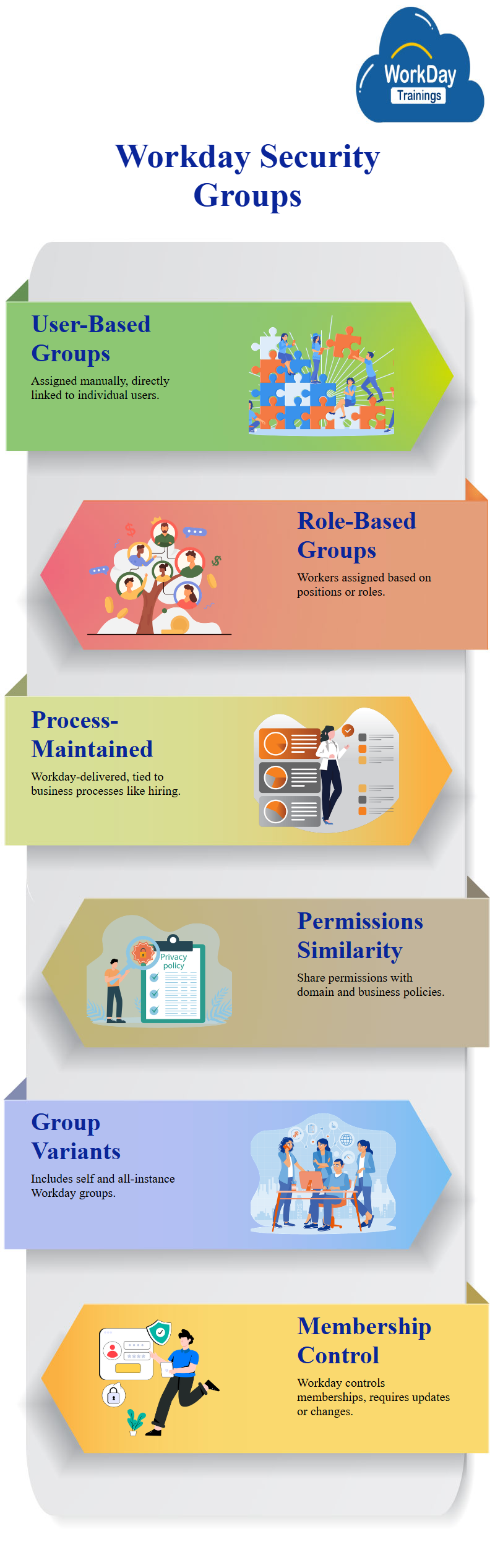
Moving on to the discussion of user-based security groups, which are different from role-based security groups.
User-based security groups are directly assigned to users and remain with them regardless of job changes. They are typically used for Workday administrator jobs, and are not job-based, role-based, or location-based.
A user-roll Workday administrator is an example of a user-based security group, where administrators are manually selected and assigned special permissions. This type of group is typically used for administrators with specific permissions.
The article concludes by discussing the differences between role-based and user-based security groups and their respective purposes.
The differences between role-based and user-based security groups.
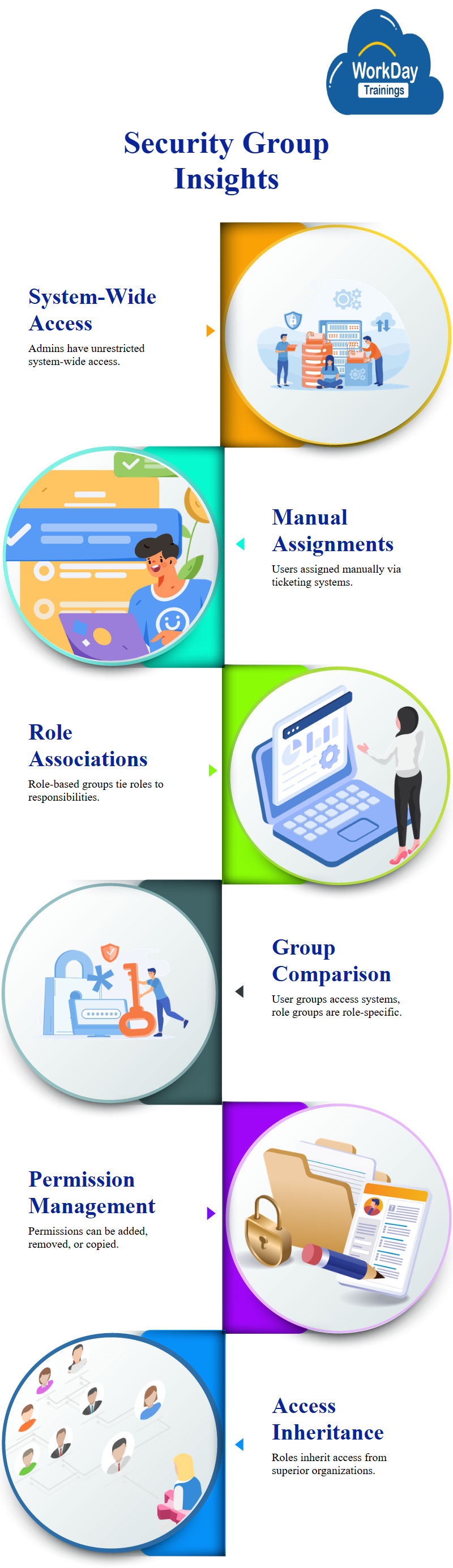
User-based security groups are unconstrained, meaning they have access to the entire system regardless of the organization they are part of.

Administrators, such as payroll admins, Workday report writer, Workday security administrator, auditors, and benefits administrators, have system-wide access.
Users are assigned to these groups manually, and organizations typically manage them through ticketing systems like Jira or Asana.
User-based security groups are suitable for administrators or specific individuals who need system-wide access for their areas of responsibility.
Examples of user-based security groups include Workday business process administrators, job and position administrators, organization admins, security admins, supervisory admins, payroll admins, Workday talent admins, comp admins, absence admins, and Workday HR auditors.
Role-based security groups group users based on their roles, which are associated with organizations and indicate the responsibility for that item.
These roles are inherited from the superior organization and grant access to specific roles, such as Workday manager roles, only for direct reports.
To compare and contrast between role-based and user-based security groups, it is essential to understand the differences and differences between the two types of security groups.
A user-based security group can access the entire organization, but role-based groups can only access specific organizations where they have the role. Users can create and assign a user to a user-based security group manually, without any role assignment.
To maintain permissions for a security group, users can choose to maintain or copy permissions from another group. Maintaining permissions allows users to add or remove permissions while copying permissions from another group allows users to copy security data from another group.
Evaluating Security in Workday View Reports
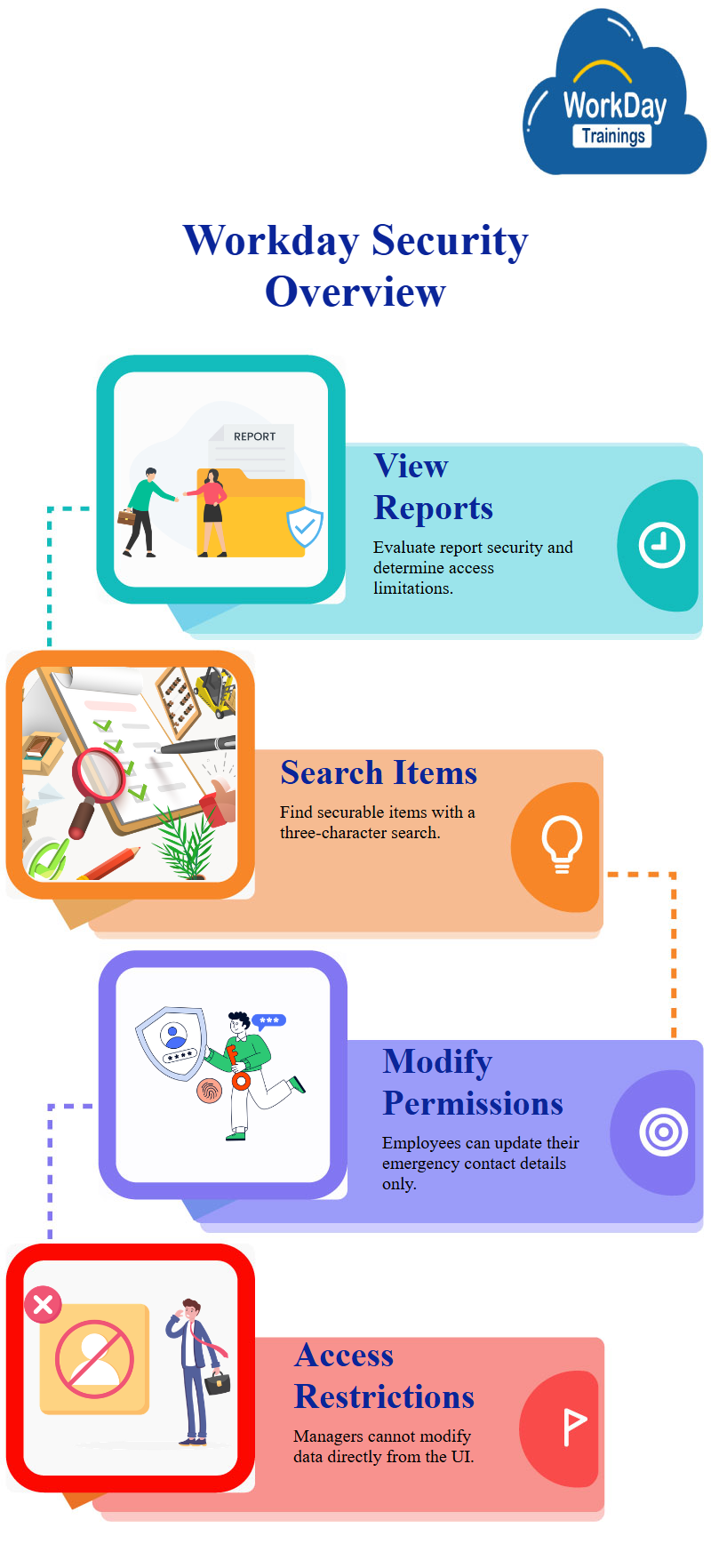
View security is a free-form text report that helps evaluate the security of delivered reports, tasks, and data sources in Workday. It allows users to search for anything in the system and determines how delivered reports are secured. To evaluate a specific securable item, users can enter at least three characters of the item and click “OK” to view results.
Workday Emergency Contact Information Handbook: Granting Modify Access to Security Policies and Permissions
Coming to the limitations of modifying emergency contact information in Workday, a system used for managing employee information. It explains that only the employee has the ability to change their contact information, not others.
The security measures that can be used to view and modify the data, such as the Workday report field for emergency contacts. The Workday integration permissions that allow the manager to view and change the data, but they are not allowed to do so from the UI.
The Workday discusses the need for the manager to have certain permissions to edit the emergency contact information, such as modified permissions.
From the above reading it can be concluded by mentioning the importance of using Workday’s terminologies when discussing the system, as it can significantly impact interviews.
For the process for granting modify access to a security policy.
Users navigates to the related actions and finds out that the policy is not enabled. They then enable the policy and confirm its activation.
The policy has pending changes, so they change the policy permissions. The manager is then given modify access, and they can now make changes to the policy information.
The manager is then able to modify emergency contacts. The security group is then able to view the report on the security group, and the emergency contacts report is found. Users can then access the security policy by clicking on the security policy field.
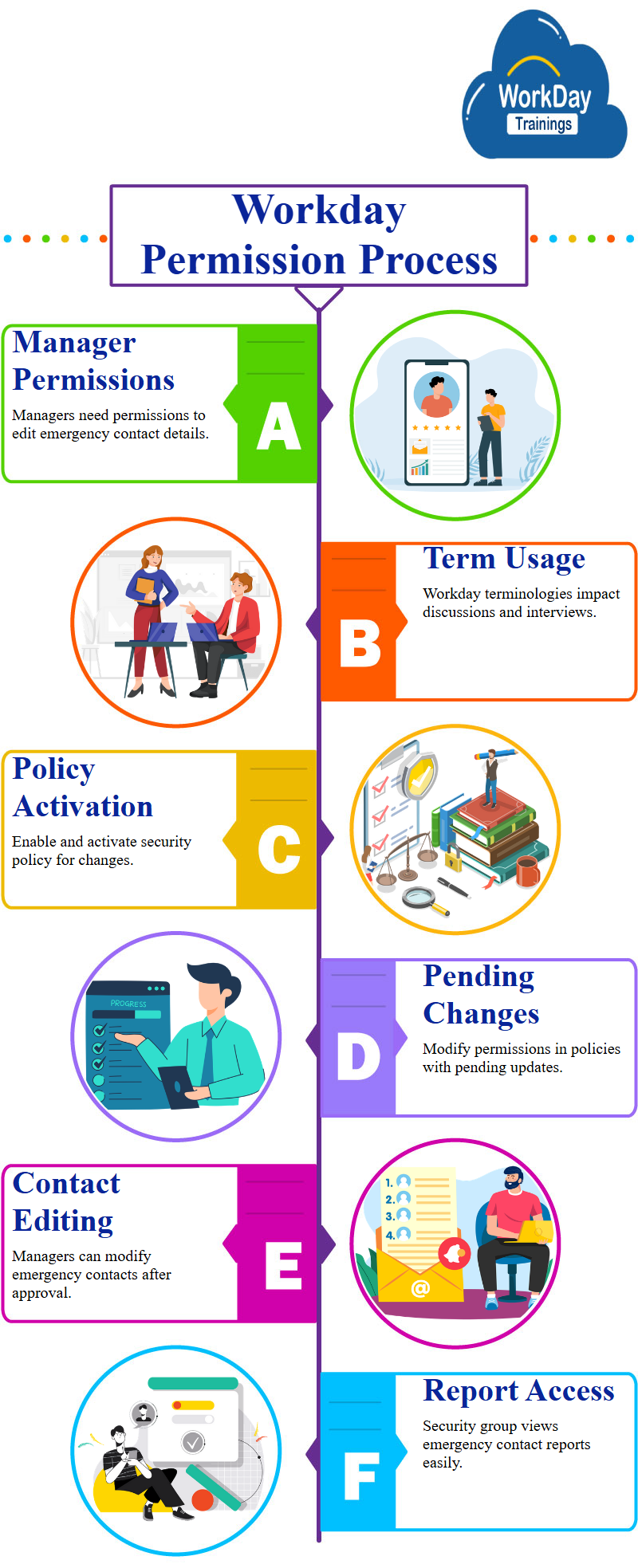
This process is used to change security policy and find out about the security. It also suggests identifying any field that has been used in eligibility criteria or assignments.
The importance of updating security policies and permissions to ensure only authorized individuals have access. The iterative process of security, which involves trial and error and requires time and testing.
Different types of security groups, including role-based, user-based, and process-maintained groups. These groups are Workday work-day delivered and can be modified by adding permissions to domain security policies.
The Tutorial emphasizes the importance of worker assignment to these groups. by discussing how workers are assigned to roles based on related actions, roles, and roles, and how they are indirectly associated with the role-based group. They also discuss how workers are assigned to user-based groups manually and directly to users.
User-based security groups are assigned directly to users, which requires manual intervention by the Workday security administrator. Role-based security groups involve assigning a worker to a position, role, or security group, granting certain permissions. User-based security groups are straightforward and can be edited directly.
Process-maintained security groups are Workday-delivered and include users based on business processes like hiring, termination, transfer, and retirement. Workday assigns workers to these groups based on the system’s decisions, such as hiring, termination, transfer, and retirement. Permissions for these groups are the same as domain and business process security policy permissions.
There are two Workday versions of these security groups: one is self, which includes all instances of the group, and another that includes all instances of the group. These groups are Workday-delivered and membership to them is controlled by Workday. It is important to be aware of these security groups as they may require changes, updates, or permissions.

Harsha
New Technology, let's explore together!

